KB
On this page
USB keystroke in Wireshark
Description
Hmm, haven’t seen this type of wireshark file in a while now.
Attachment: challenge.pcapng
Solution
We were given a pcap file for this challenge. However, it has different protocols compared to what we normally see.
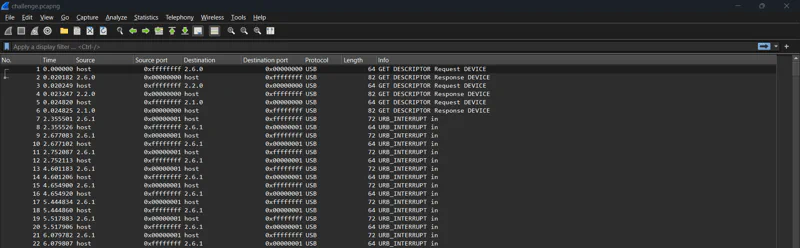
Note that the captured packets are using USB protocol. Since we are not familiar with this kind of packet capture, let’s try to find for similar CTF writeups (if there’s any).
We found some useful websites and videos for similar challenges. It says that we have to record all the keystrokes captured.
tshark -r challenge.pcapng -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capdata | sed
's/../:&/g2' > keystrokes.txtWe can use tshark to get the keystrokes we want.
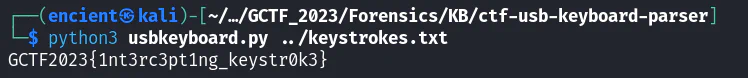
Then we use a keystroke parser to parse all the keystroke and display it.
Flag
GCTF2023{1nt3rc3pt1ng_keystr0k3}